Having talked about spamming, in this post, I would like to shortly discuss about phishing, a technique for identity theft, which in my personal experience, has become more rampant these days.
If it is the first time for you to read this fancy term, phishing is an attempt to steal somebody else’s sensitive information such as username, password, credit card details, and other personal credentials usually done by sending an email containing a false claim to the target. The content can be a threat, warning, and other form of falsified truth carefully crafted to encourage the target to submit his personal credentials. As you may have predicted, phishing was derived from “fishing”. The “fisher” is the person who wants to steal the information and the target is the “fish”. The false claim is obviously the “bait” used to attract and hook the “fish”.
Identity theft is disadvantageous and can sometimes become disastrous to the victim. Let us take a case of a phishing attempt from a sender who falsely claims as your email account provider. The message contains warning to verify your email account by supplying your user account id and password. If you inadvertently submitted the requested information to this site, you might have never imagined how creative the phisher is in exploiting this private information they stole from you.
One of my colleagues was a victim of phishing. After the adversary obtained my colleague’s credentials, the person tampered with his account and solicited immediate financial aid to his friends by sending email that described an emergency situation he was facing. In reality, it was absolutely untrue. Fortunately, one of his friends was suspicious enough to realize the bizarreness of the request. That guy tried to contact my colleague directly to confirm the request and when it was found that he never wrote such email, they realized that somebody had compensated his account. To solve the problem, he scanned his PC and laptop, retrieved and changed the password for his account and notified all his contacts about his account misuse and informed them to ignore the money request.
In his case, he was a bit lucky since he found the account misuse early. But what if the situation were worse than this? You can imagine any scenarios that might happen.
To avoid being victimized in a phishing attempt, I will provide this quick guide to you. I use an example of LinkedIn phishing attempt delivered into my inbox.
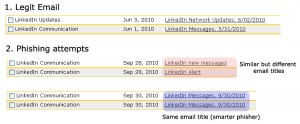
1. Look carefully at the title of the message. Compare with other message title of the same topic if necessary.
If you regularly receive email from an opt-in service, you will notice if there is slight difference between a fraudulent one and a legit one. But be careful, sometimes the phisher is also smart by crafting a phishing email with the same title as the legit one.
2. Match the sender’s email address with the authority s/he claims. If your mail application enables you to see the Full Header of the email, use this feature.
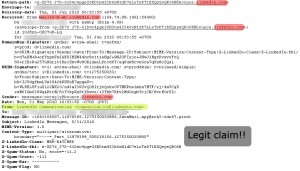
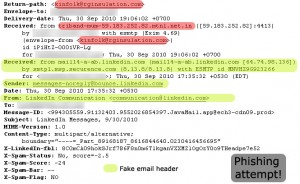
Scanning through the email header and find out who’s sending you an email should only take few seconds. It will not hurt your busy schedule. Moreover, you may be curious if a supposed-to-be-an-IT-savvy authority or company ask you to supply your username and password to their system. They should never need it as they already keep your data with them. Under this circumstance, you might be interested in finding out who the real sender is. Check the full header of the email, and make sure that the email was sent from the same domain name with the authority website.
Below, you can see the comparison of email header from a legit sender and from a person trying to steal your information.
a. Legit header and full header
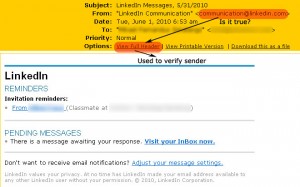
b. Header and full header of a phishing email
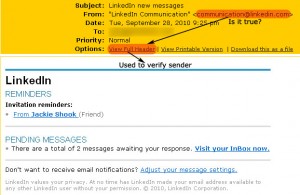
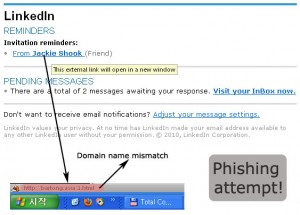
3. Hover your mouse over the links and ensure that a) the link is a direct link and b) the link points to the same domain with the authority claimed by the sender.
Before you click a link, it is wise to hover on it and see if there is a match between the authority domain and the domain name shown at the status bar of your browser. If there is domain name mismatch, you should be alert that somebody is trying to lure you into opening a harmful website or application that may end with your personal information being stolen.
4. If possible, use a better spam filtering software.
Better spam filtering software should have prevented spam, phishing, fraudulent emails from reaching your inbox and getting read. If you happen to see frequent spam filtering breach, you may consult with your system administrator and ask him to improve the spam filtering system.