Once said that high trees are prone to swift wind. When it comes to managing website, increasing traffic in most cases leads to increasing security threats. Even though the website contains good content and is useful to certain niche or broader audience, no exact guarantee can be made that the site is 100% secure, fully shielded and armored and will never be compromised. Site owner will never know how much his site attracts undaunted cyber ghosts to come and test the site’s security.
Since internet is the biggest library, one can get information about security breach in certain application quickly in easy manner. Search engines provide all the information, either good or bad, and perform quick search for keyword. With sufficient knowledge of exploiting search engine, one can locate where the security breach is, find the target sites, and test the water until the site gets compromised. With such easy access to exploits and hacking tools, one doesn’t need to be tech savvy to manually find the security holes. It will be even easier when the target sites use popular open source solutions because all bugs and holes are documented.
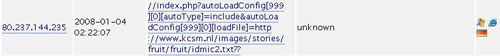
Let me share the same problem I face on this site. Once when I was looking at the access log, I got interesting query as depicted below:
The attacker tried to perform hacking attempt by exploiting remote file inclusion bug in ZenCart. What’s interesting is, the exploit is located within a joomla site. The joomla site might have also been compromised, but I won’t draw any conclusion about that.
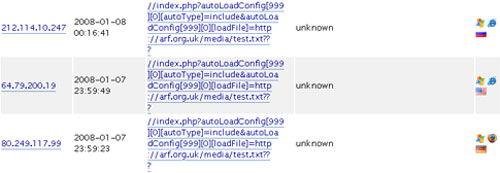
I didn’t know how the attacker collected footprints of this site and later came with a conclusion that ZenCart is installed and used (it can also be that it’s a bot though). I simply ignored those attempts and considered them as random attempt, until I read the newer logs. This time, the attacker used proxies to perform the action.
And surprisingly, it was the same exploit with different remote file.
Moral of the story: if the site is important for you, harden the site by enhancing the security. Update regularly if you’re using open source applications. Don’t forget to backup all data because you won’t know how severe the damage is when the site is finally compromised.